Detect Amazon Bedrock Misconfigurations with Datadog Cloud Security
Sources: https://aws.amazon.com/blogs/machine-learning/detect-amazon-bedrock-misconfigurations-with-datadog-cloud-security, https://aws.amazon.com/blogs/machine-learning/detect-amazon-bedrock-misconfigurations-with-datadog-cloud-security/, AWS ML Blog
TL;DR
- Datadog Cloud Security now provides detections and remediation guidance to identify and fix Amazon Bedrock misconfigurations before they become security incidents.
- The integration uses both agentless and agent-based scanning to continuously monitor your AWS environment for misconfigurations, identity risks, vulnerabilities, and compliance violations, prioritized by a Datadog Severity Scoring system.
- A representative risk is publicly writable Amazon S3 buckets used to tune or customize Bedrock models, which could enable data poisoning if accessed by threat actors; Datadog offers out-of-the-box detections and remediation steps to mitigate this.
- The solution leverages live Cloud Map diagrams to contextualize AI risks alongside sensitive data exposure and other security signals, improving clarity and response speed.
- The Datadog–AWS partnership extends across 900+ integrations, enabling out-of-the-box AI security coverage within a broader cloud security strategy. This approach follows the AWS Shared Responsibility Model, with AWS managing infrastructure security and customers responsible for secure configurations and access controls inside their Bedrock environments. For more details, see the source post from AWS and Datadog.
Context and background
As organizations increasingly adopt Amazon Bedrock for generative AI applications, securing its usage becomes essential. Bedrock delivers enterprise-grade security by incorporating built‑in protections for data privacy, access controls, network security, compliance, and responsible AI safeguards. Customer data is encrypted in transit (TLS 1.2 or higher) and at rest with AWS KMS, with customers retaining full control over encryption keys. Data privacy is central: inputs, prompts, and outputs are not shared with model providers nor used to train foundation models. Fine-tuning happens on private copies of models, ensuring data confidentiality. Access is tightly governed through AWS IAM and resource-based policies, enabling granular authorization for users and roles. Bedrock integrates with AWS PrivateLink and supports VPC endpoints for private, internal communication, so traffic does not leave the Amazon network. The service complies with ISO, SOC, CSA STAR, HIPAA eligibility, GDPR, and FedRAMP High, making it suitable for regulated industries. Guardrails filter sensitive or harmful content to promote responsible AI use. Security follows the AWS Shared Responsibility Model, where AWS manages infrastructure security and customers manage secure configurations and access controls within Bedrock. Datadog and AWS have partnered to provide a holistic view of AI infrastructure risks, vulnerabilities, and data exposures. Datadog Cloud Security employs both agentless and agent-based scanning to help organizations identify, prioritize, and remediate risks across cloud resources. The integration enriches findings with observability data, strengthening overall security posture in AI implementations. As more organizations accelerate their AI adoption, embedding security into existing processes becomes critical, especially as regulations tighten. More details on why the Bedrock integration was pursued come from the AWS and Datadog collaboration within the AWS Bedrock ecosystem. During Q4 2024, Datadog Security Research observed rising threat actor interest in cloud AI environments, highlighting the timeliness of this integration. By combining Bedrock’s AI capabilities with Datadog’s security expertise, teams can accelerate AI adoption while maintaining robust controls.
What’s new
Datadog and AWS have expanded into three core capabilities within Datadog Cloud Security to protect Bedrock deployments:
- Holistic AI security: Integrates AI security into your broader cloud security strategy, contextualizing AI risks with other security signals such as identity exposure and misconfigurations.
- Real-time risk detection: Detects potential AI-related security issues as they emerge, enabling faster response and remediation.
- Simplified compliance: Provides pre-built detections and remediation guidance to help meet evolving AI regulations. This partnership enables detections for Bedrock customers and integrates with Cloud Map to visualize live diagrams of cloud architecture, placing AI risks in the context of surrounding infrastructure and data flows. Datadog’s agentless scanning further ensures continuous visibility by monitoring AWS environments at intervals between 15 minutes and 2 hours. Beyond Bedrock-specific detections, the system uses a catalog of hundreds of out-of-the-box rules to identify misconfigurations and threat paths that adversaries can exploit, all while maintaining the broader security context across the AWS environment.
Why it matters (impact for developers/enterprises)
For developers and enterprises, this integration offers concrete benefits as AI becomes more pervasive:
- Accelerated secure AI adoption: By embedding AI security into existing cloud security workflows, teams can innovate faster without compromising controls.
- Early risk visibility: Real-time detections with contextualized risk scores help teams focus on the most significant issues, reducing noise and speeding remediation.
- Improved compliance posture: Pre-built detections and remediation workflows support regulatory alignment and internal governance, with posture scores reflecting resolved findings.
- Scalable security coverage: Datadog’s long-standing integration ecosystem (more than 900 integrations) and cloud security expertise enable scalable monitoring across hybrid and multi-cloud environments. Customers can view issues alongside surrounding infrastructure using Cloud Map, enabling teams to see how Bedrock resources interact with other AWS resources and data stores. The security model emphasizes strong encryption, private networking, and strict access controls, which are central to maintaining secure AI workloads in regulated industries.
Technical details or Implementation
- Scanning approach: Datadog Cloud Security supports both agent-based and agentless scanning to detect misconfigurations, identity risks, vulnerabilities, and compliance violations in AWS resources.
- Scheduling: Agentless scanning runs at configurable intervals ranging from 15 minutes to 2 hours, enabling timely detection as configurations change.
- Risk scoring: Findings are prioritized using the Datadog Severity Scoring system, which considers production status, public exposure, and access to sensitive data to reduce noise and emphasize critical issues.
- AI-focused detections: The system includes Bedrock-specific detections, such as identifying publicly writable S3 buckets used for training or fine-tuning Bedrock models. If such a misconfiguration exists and the bucket contains data used for model training, a data poisoning risk could arise.
- Remediation guidance: Datadog automatically provides step-by-step remediation guidance for each finding, with options to fix configurations directly in AWS, create Jira tickets, or trigger built-in workflow automation. Remediation actions update in Datadog and can be verified to improve the posture score.
- Cloud architecture visibility: Cloud Map diagrams provide live visuals of cloud resources and their relationships, giving context to AI risks within the broader infrastructure.
- Guardrails and privacy: Bedrock includes configurable guardrails to filter sensitive or harmful content, aligning with responsible AI practices. Data privacy measures ensure inputs, prompts, and outputs are not shared with model providers or used to train foundation models, and data encryption is supported in transit (TLS 1.2+) and at rest (AWS KMS).
- Deployment options: Datadog Cloud Security can be deployed agentlessly, with the Datadog agent, or with both, to maximize coverage across the AWS environment.
- Compliance and standards: Bedrock complies with a range of industry standards, including ISO, SOC, CSA STAR, HIPAA eligibility, GDPR, and FedRAMP High, making it suitable for regulated industries. These capabilities build on Datadog’s existing cloud security expertise and the established integration with AWS, enabling a unified view of AI infrastructure risks and a faster path to secure AI deployments.
Key takeaways
- Datadog Cloud Security adds Bedrock-specific detections and remediation guidance to secure AI workloads.
- The solution provides real-time risk detection, holistic AI security, and simplified compliance with pre-built detections.
- Detects and prioritizes issues using a multi-layer risk score that includes production status, public access, and data sensitivity.
- Remediation is actionable and integrated, with options to fix in AWS, open Jira tickets, or use workflow automation.
- The approach leverages live Cloud Map views to contextualize AI risks within a broader cloud architecture.
FAQ
-
What is Amazon Bedrock and why is it relevant to Datadog Cloud Security?
mazon Bedrock is a fully managed service that makes high-performing foundation models from leading AI companies and Amazon available through a unified API, making it an ideal starting point for Datadog’s AI security capabilities. See the AWS blog for details.
-
How does Datadog Cloud Security detect Bedrock misconfigurations?
It uses both agentless and agent-based scanning to identify misconfigurations, identity risks, vulnerabilities, and compliance violations, with findings prioritized by the Datadog Severity Scoring system.
-
What specific risk is highlighted in Bedrock deployments?
Publicly writable S3 buckets used for Bedrock training or fine-tuning can lead to data poisoning if misconfigured; Datadog provides out-of-the-box detections and remediation guidance.
-
How can teams remediate detected issues?
Remediation steps can be performed directly in AWS, via Jira tickets, or through built-in workflow automation, and the remediation updates are reflected in the posture score.
-
How often are scans run?
gentless scans run at intervals between 15 minutes and 2 hours, allowing timely detection as configurations change.
References
More news
First look at the Google Home app powered by Gemini
The Verge reports Google is updating the Google Home app to bring Gemini features, including an Ask Home search bar, a redesigned UI, and Gemini-driven controls for the home.
Shadow Leak shows how ChatGPT agents can exfiltrate Gmail data via prompt injection
Security researchers demonstrated a prompt-injection attack called Shadow Leak that leveraged ChatGPT’s Deep Research to covertly extract data from a Gmail inbox. OpenAI patched the flaw; the case highlights risks of agentic AI.
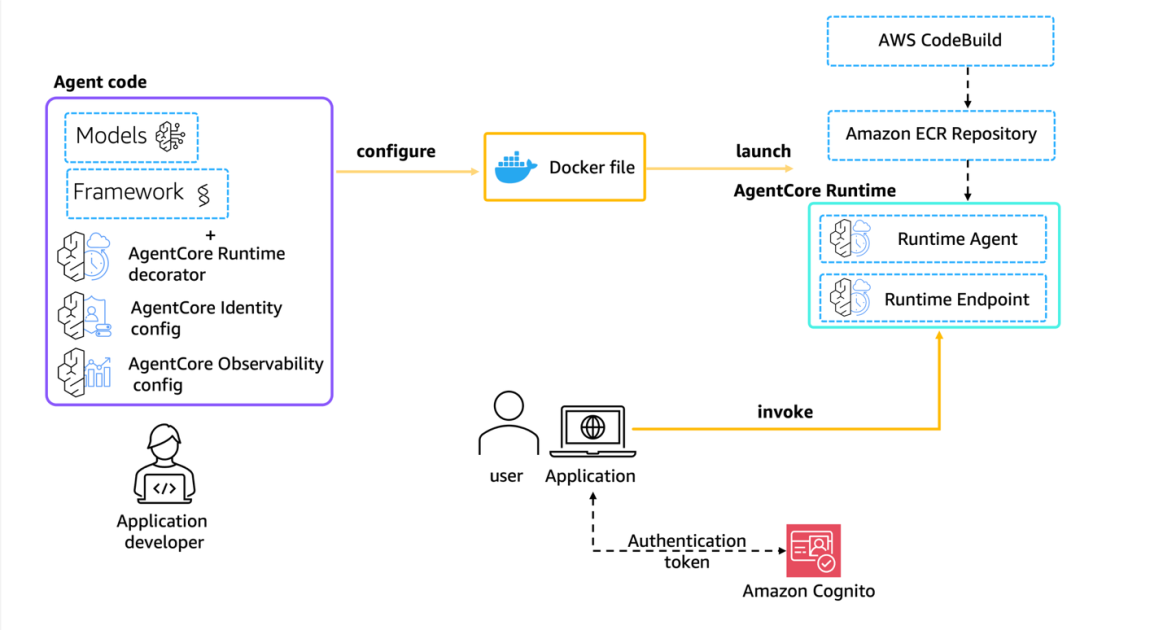
Move AI agents from proof of concept to production with Amazon Bedrock AgentCore
A detailed look at how Amazon Bedrock AgentCore helps transition agent-based AI applications from experimental proof of concept to enterprise-grade production systems, preserving security, memory, observability, and scalable tool management.
Predict Extreme Weather in Minutes Without a Supercomputer: Huge Ensembles (HENS)
NVIDIA and Berkeley Lab unveil Huge Ensembles (HENS), an open-source AI tool that forecasts low-likelihood, high-impact weather events using 27,000 years of data, with ready-to-run options.
Scaleway Joins Hugging Face Inference Providers for Serverless, Low-Latency Inference
Scaleway is now a supported Inference Provider on the Hugging Face Hub, enabling serverless inference directly on model pages with JS and Python SDKs. Access popular open-weight models and enjoy scalable, low-latency AI workflows.
Google expands Gemini in Chrome with cross-platform rollout and no membership fee
Gemini AI in Chrome gains access to tabs, history, and Google properties, rolling out to Mac and Windows in the US without a fee, and enabling task automation and Workspace integrations.